
IoT Security – Keep Software Up to Date
IoT Security: Keep Software Up to Date Internet of Things (IoT) devices are vulnerable to security breaches. Install software updates and security patches as soon


IoT Security: Keep Software Up to Date Internet of Things (IoT) devices are vulnerable to security breaches. Install software updates and security patches as soon

Protect Eyes From Blue Light Screens emit blue light which can keep you up at night. Change your display settings on Windows. Go to: Settings

Share YouTube Video at a Precise Point Click the Share button below the YouTube video and check the checkbox below the link. It will automatically

Use a Password Manager Use a Password Manager to create, store, and sync complex passwords across multiple devices. Password managers only require you to remember

Open Link in New Tab While on an internet page, use the mouse wheel to middle-click on a link to open the link in a

Crop an Image Right-click an image in a Microsoft Office file and select the crop button. Select the side or corner cropping handle and drag

IoT Security: Change Default Passwords Many Internet of Things (IoT) devices come with default passwords that are easy to guess. Change these passwords to strong,

Select It All In Excel, click in the first cell that you want to select and hold down Ctrl+Shift+End. The cursor will jump to the

Resize Image Proportionally To maintain the proportions and keep the center in the same place when resizing an image in a Microsoft Office file, press
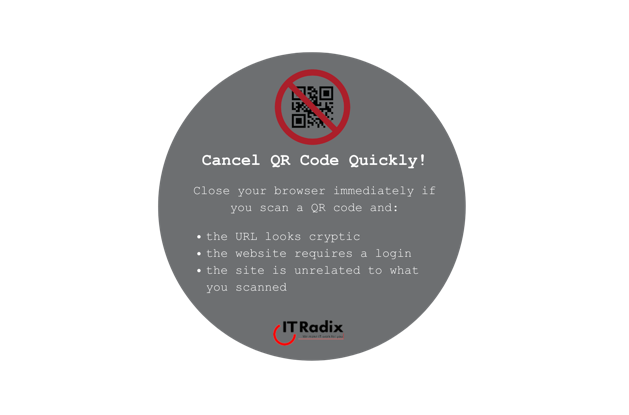
Cancel QR Code Quickly! Close out of your browser immediately if you scan a QR code and: the URL looks cryptic the website requires a
"*" indicates required fields