
October 2024 IT Radix Resource Newsletter
In this issue:
- Monsters Lurking in the Digital World
- Deepfakes Are Coming to the Workplace
- End of Life: The Final Countdown


In this issue:

What to Do If You’ve Been Hacked Imagine this… You realize you just clicked on a suspicious email from someone claiming to be a Nigerian

A Business Continuity Plan (BCP) Ensures That the Unexpected Doesn’t Slow You Down You can’t predict when a business disaster may happen, but a Business

Modern Cybersecurity is About Continuous Improvement One of the most significant challenges to cybersecurity initiatives today is the belief that “current security is good enough.”

Team Up with IT Radix for Managed Services and Get Your IT Game On In the competitive arenas of business and NFL football, organizations face

In this issue:
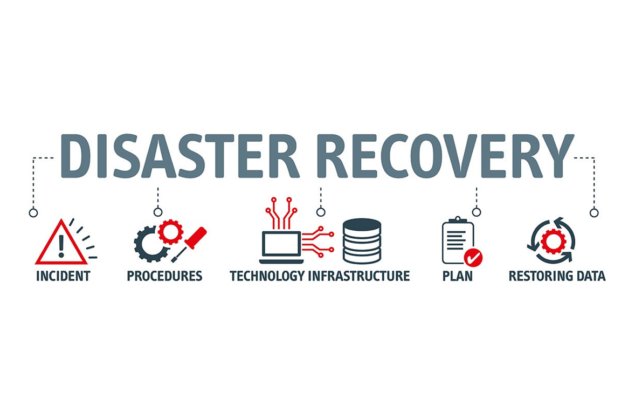
Disaster recovery planning is an ongoing process. Be prepared to handle unexpected disruptions by following these seven steps: 1. Written Plan and Documentation: Review and

IT Radix’s Proactive Approach to IT Support The continuing stream of news events seem to happen so fast these days that some of us may
We all value work and family balance. But during the holidays, that seesaw tends to teeter more toward family, even when end-of-year deadlines hang over
“In the Summertime” is a 1‑hit wonder from 1970 by a band called Mungo Jerry. It reached #1 in the charts around the world selling
"*" indicates required fields