
The #1 Mistake Companies Make With Their IT
If you’re like many businesses today, there’s a good chance you’ve made this one mistake with your IT security: you don’t budget for it. Or


If you’re like many businesses today, there’s a good chance you’ve made this one mistake with your IT security: you don’t budget for it. Or

Building a successful relationship with your MSP (Managed Service Provider) creates value for your business. Today’s businesses rely on a solid foundation of technology to

Quick Tip: If you cannot enable multi-factor authentication, change your passwords frequently We’re continuing to explore the topic of passwords and how they help keep
Many will remember the character Tattoo, from the TV show Fantasy Island. He was famous for calling out “The plane! The plane!” as the seaplane

As annoying as spam email is, it’s usually pretty harmless. But hackers have been using a method called distributed spam distraction (DSD) where spam email

Identity theft is a form of fraud where a person pretends to be someone else in order to access resources in that person’s name. Akin
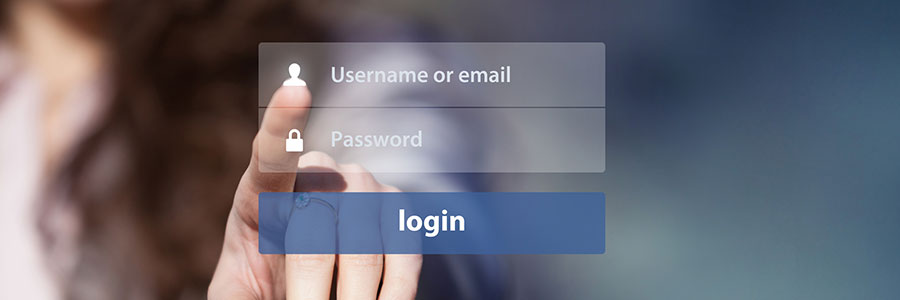
The National Institute of Standards and Technology (NIST) once said that a good password consisted of three things: upper- and lowercase letter, numbers, and symbols.

Scanning the files you download is not enough to detect malware these days. Hackers have found a clever way to get around antivirus and anti-malware
Quick Tip: Separate work and personal accounts/devices as much as possible. Why: If you’re using a company device to access a compromised account, you’re opening

As almost every organization has undergone dramatic changes in their Information Technology (IT) framework over the past few months, we noticed a lot of things:
"*" indicates required fields