
What you need to know about VoIP phishing
Scammers have found a way to exploit vulnerabilities in VoIP (Voice over Internet Protocol) via a scam called vishing. This scam works much like any


Scammers have found a way to exploit vulnerabilities in VoIP (Voice over Internet Protocol) via a scam called vishing. This scam works much like any

If you think your email is safe from hackers, think again. A lack of sufficient email security measures can result in data theft, unauthorized access

Cybersecurity is everyone’s responsibility. But you don’t need to be an IT expert to know how to protect yourself from a cyberattack. To help you

Phishing scams have been around for years, and they’ve gotten smarter with time. Recently, criminals have been targeting iPhone users through a voice phishing scam

The volume of malicious cyber attacks is increasing every year. Although many companies use the latest network security systems, they aren’t immune to the hackers’

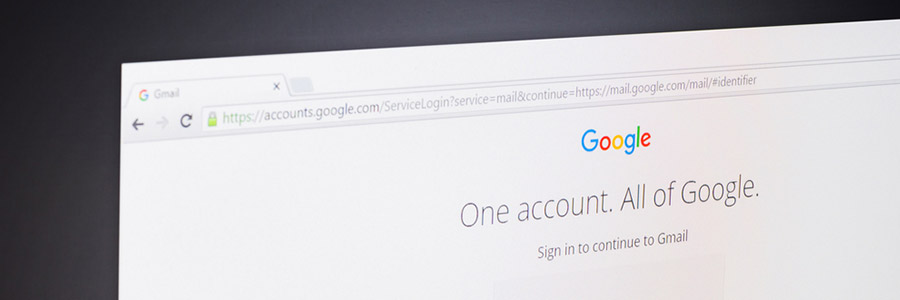
Phishing scams disguise malicious links and emails as messages from trusted sources. The most recent scam to watch out for almost perfectly imitates a trusted

Cybercriminals have been relentless throughout 2017. In the past couple of months, hackers discovered new malware strains and software vulnerabilities that have overwhelmed thousands of

No one can escape the news of WannaCry. The IT industry has been covering this type of malware for years, but never has one campaign
As the technology that recognizes and thwarts malware becomes more advanced, hackers are finding it much easier to trick overly trusting humans to do their

Software developers and hackers are in a constant game of cat and mouse. When cybercriminals find new security bugs to exploit, tech companies have to
"*" indicates required fields