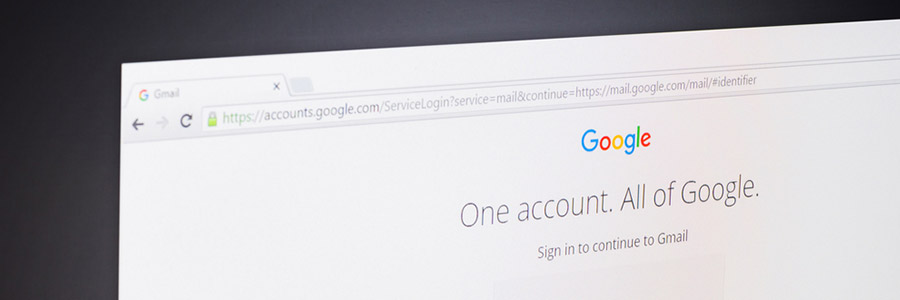
The most advanced Gmail phishing scam yet
As the technology that recognizes and thwarts malware becomes more advanced, hackers are finding it much easier to trick overly trusting humans to do their


As the technology that recognizes and thwarts malware becomes more advanced, hackers are finding it much easier to trick overly trusting humans to do their

Protect or purge digital files as you do important paper files. Sensitive materials such as hard drives, disks and memory cards should be shredded. Clean

Every now and then, we need to reset the conversation about virtualization and review how it works in its most basic form. With so many

Eavesdropping is the intentional act of secretly listening in on a conversation, usually not for the best of intentions. Although today the act also includes

Mac Pro users have long awaited the release date of the new workstation, and who could blame them when the current model has been available
Be prepared…we all know this as the Boy Scout motto. And candidly it could also be a motto or refrain you would hear from the

The keepers of the Parrot Gardens at the Vancouver Zoo thought they had it all under control in 2009. Clip the wings of all the

Software developers and hackers are in a constant game of cat and mouse. When cybercriminals find new security bugs to exploit, tech companies have to
No computer is safe from malware, not even Macs. Even though incidences of viruses and malware are rare for Apple computers, they can still occur

Most phishing attacks involve hiding malicious hyperlinks hidden behind enticing ad images or false-front URLs. Whatever the strategy is, phishing almost always relies on users
"*" indicates required fields